SAGA: S ynthetic A udit Log G ener A tion for APT Campaigns
News!
- Jun 2024 Update SAGA dataset - v2.0!
- Feb 2024 Update SAGA dataset - v1.0!
What is SAGA?
SAGA can generate configured synthetic audit logs for any arbitrary time interval to embed stealthy APT attacks. Here, we are releasing serveral large-scale set of synthetic audit logs designed to simulate APT campaigns.
SAGA has several features:
|
|
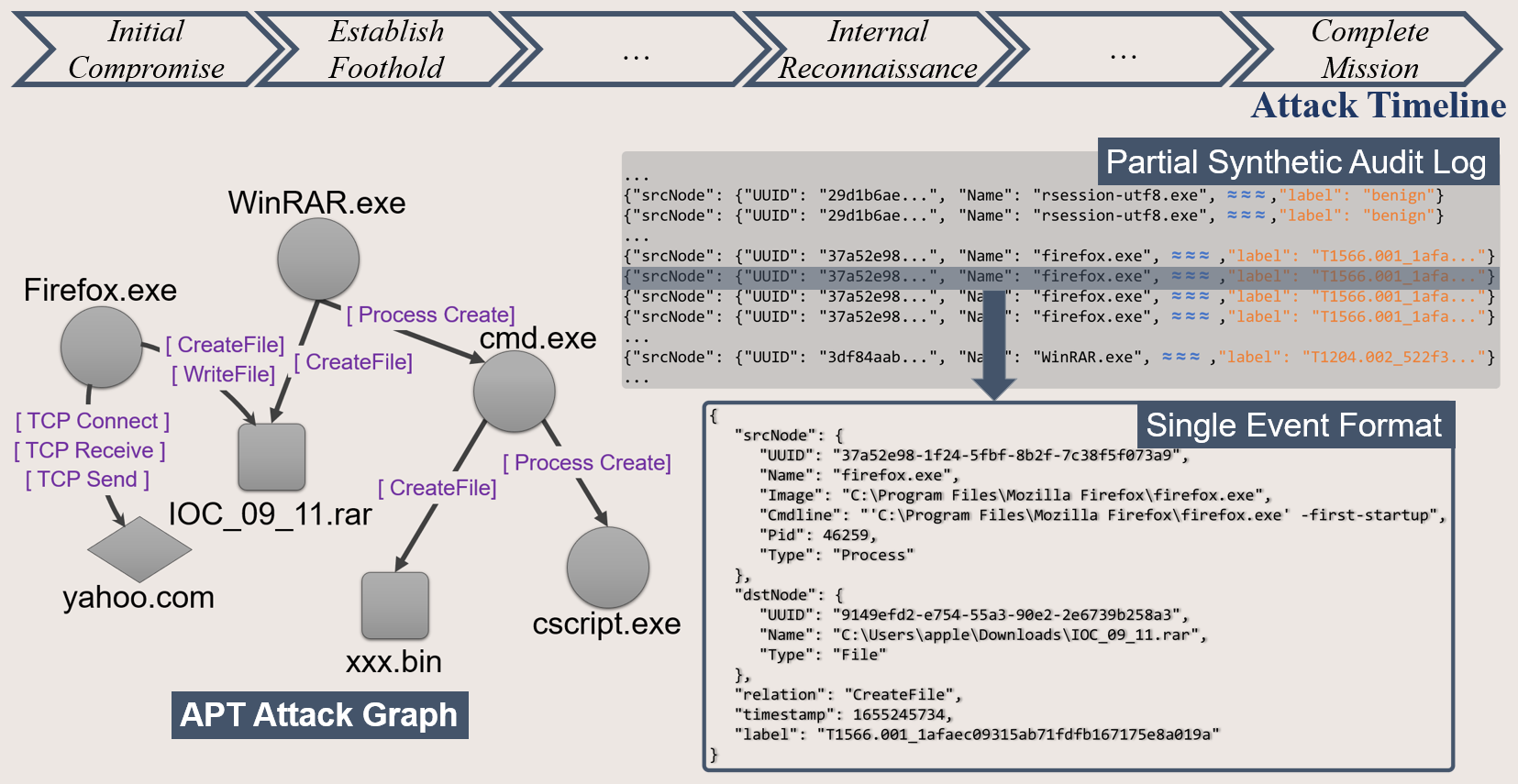
Example
SAGA demonstrates an attack scenario from APT28 along with Mandiant adversary lifecycle.
In the initial stages of the attack, phishing emails containing malicious attachments are sent to the victim to download the attachment IOC_09_11.rar. This activity is designated as the Technique T1566.001 Spearphishing Attachment of the attack lifecycle stage Initial Compromise.
This malicious attachment exploits a vulnerability in WinRAR versions below 6.23 (as mentioned in CVE-2023-38831). When the victim clicks on the IOC_09_11.rar file, it triggers subsequent malicious activities designated as T1204.002 User Execution: Malicious File of the attack lifecycle Establish Foothold.